Cybersecurity Force Multiplier
Ensure the security and configuration of your AWS, Azure, or Google Cloud environments with ICE Cybersecurity's Cloud Security Assessment. Our platform connects to your cloud environment and evaluates your security posture against thousands of checkpoints. Using your cloud’s native APIs, we gather configuration data and highlight risks, giving you a simple view of your attack surface. Our automated approach saves you from navigating countless admin pages and our security experts help interpret the findings, guiding you toward the most important actions.
Types of Pen Tests
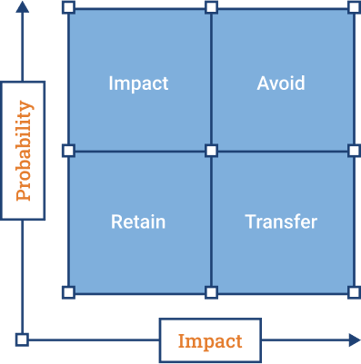
Risk Management
Identify, classify, and manage the risks. ICE works in tandem with your team to determine risk areas, tolerance and budget and build a roadmap that reduce the potential impact that keeps you up at night. Thatcan be with training your employees, connect you with insurancebrokers, build a contingency plan, or help avoid the risk.
ICE ARMs You
ICE ARMs your company with a complete security program
to protect your business. Our process is simple:
to protect your business. Our process is simple:
A
Assess
Start by understanding your drivers for security and assess your organization against relevant standards, best practices, and regulations. We don’t just point out your flaws, we provide solutions on a roadmap that fits your business.
R
Remediate
You cannot fix every gap all at once,nor should you fix all gaps. The secretis knowing the right risk to remediateat the right time. Our platform andteam help optimize your time andbudget to maximize your security ROI.
M
Manage
Visibility, accountability, and control.Our platform keeps your securityprogram tuned up and continuouslylooks for risks that could harm yourbusiness. Keep eyes on your securityprogram, demonstrate compliance andmanage your risk.
Ready to get started?
We recommend starting with an attack surface assessment. This helps find vulnerabilities and allows you to see where we can make your company more secure and confident.

